How do Dediki hack?
 Gradually, the popularity of dedicated servers leads to the fact that the demand for them is increasing at a rapid pace.
Gradually, the popularity of dedicated servers leads to the fact that the demand for them is increasing at a rapid pace.
If previously there were numerous free «dediks» in the distributions hung for several days, but now such a «freebie» picked up within a few minutes.
It is logical that users are trying to find other ways to get free «dedicated space» (dedicated server).
If buying a server for money is of little interest to users, then distributions on thematic forums and Internet sites are something that they try not to miss under any circumstances.
In general, now there is no shortage of active servers for remote actions with it, since various hacking methods are used to obtain it.
In this article we will look in detail at the most correctoptions for getting a dedicated server for free.

We send accounts in just 5 seconds to your e-mail address!

Accounts can be downloaded in your personal account, by mail without registration or immediately after payment!
We automatically create a personal account with the history of all your orders

A long time to check the goods up to 1-24 hours ( Note for tabs )

We can find accounts of any social network and postal service, service, forum

Our accounts work steadily on most types of proxy
Examples of programs for hacking Dedikov
Let us immediately note that it is unlikely that it will be possible to hack access to Dedik without using third-party programs and utilities.
Therefore, we will consider the most effective programs for hacking.
So,Dedik hackingis possible using the following utilities:
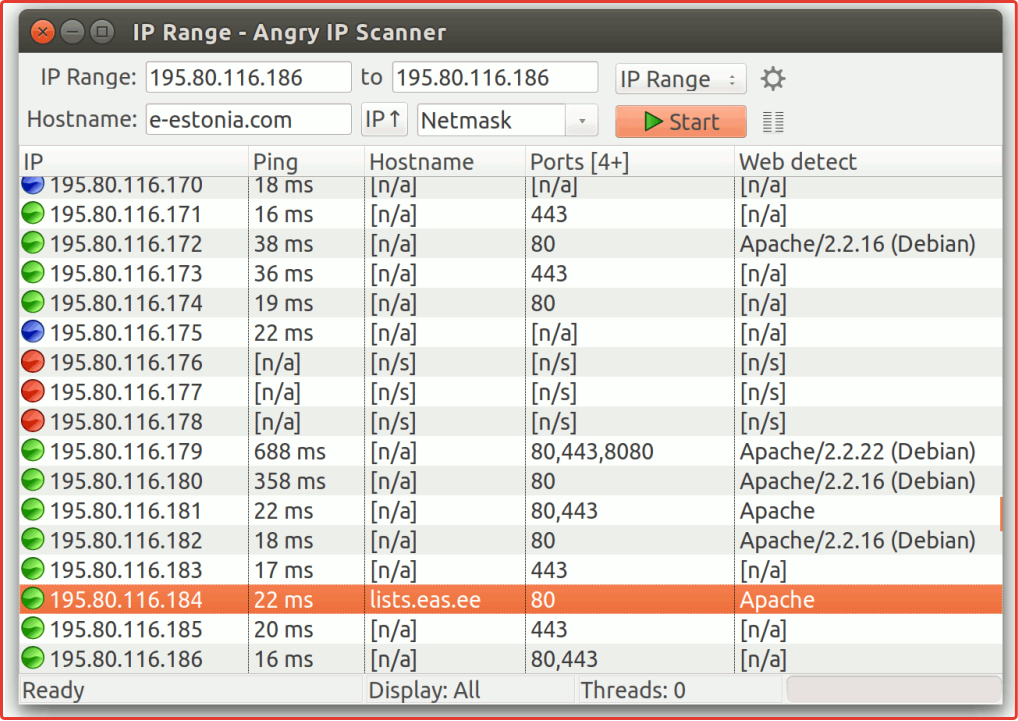
- Utility «Angry ip Scanner». The main task of the program «Angry ip Scanner» - obtaining the IP address of a specific device on the desired computer network.
To start searching for the required IP, you need to load the address database and start the selection.
The utility's interface is simple and clear, since the entire main screen of the application is occupied by the functionality of searching for the desired address.
-
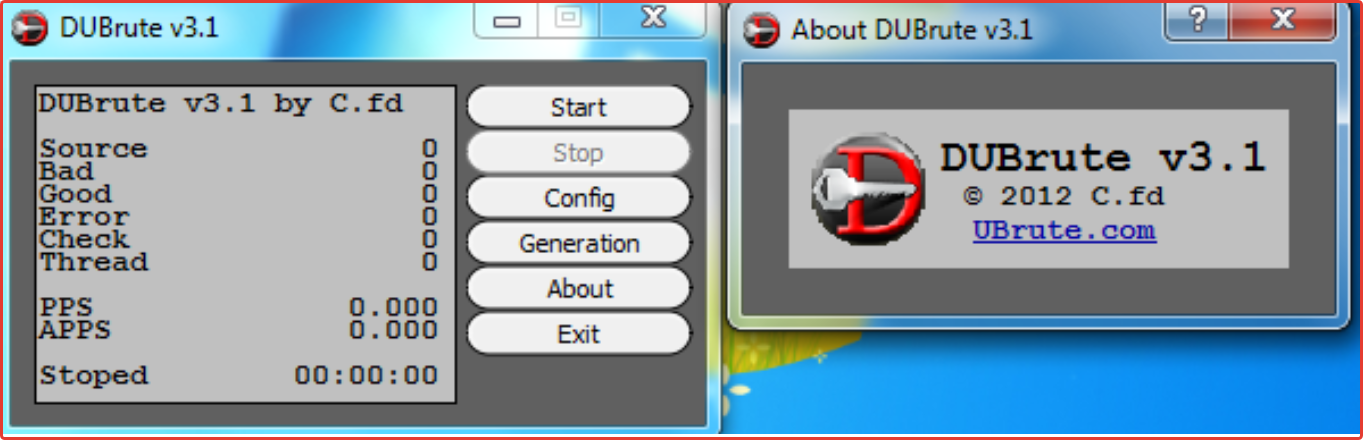
The following program, which is often used to guess a password using the brute force method – DUBrut.
-
The utility is ideally adapted for hacking Dediks, so it is often used even by professional «hackers».
-
Many versions of the utility are distributed in English, but this does not affect its use in any way
-
Another application for the brute force of grandfathers – «nlbrute».The functionality of the utility is highly stable, supporting up to 500 threads and fast password brute force.
-
In the second case, everything depends on the speed of your Internet connection.
-
Another advantage of the program is its optimization – use «nlbrute» possible on any version of Windows.
-
The next program that will be necessary for those who create accounts on Dedik is xDedic RDP.
-
By and large, the main task of the utility is to generate passwords and logins fornew accounts.Most often used for large volumes of brut.
On pages with hacker software you can often find articles with information onhow to hack Dediks through vulnerabilities.
For example, on the hacker portalhttp://www.hackersoft.ru/info/590there is detailed material on hacking using server vulnerabilities.
In general, hacking a server for personal use is quite easy if you have the necessary information and programs.
On the expanses of thematic forums on software and hacking of accounts and servers.
There are detailed manuals on how to gain access to all types of dedicated servers. Next, we will look at step-by-step instructions for one of the methods of hacking Dedik.
Instructions for hacking Dedikov
If you are interested in a free remote server, we recommend hacking Dedik using vulnerabilities.
Detailed instructions for mining Dedik running Windows are posted on the thematic hacker forum, at the linkhttps://xakep.ru/2011/05/14/57047
Next, let's look at the standard and most effective way to hack Dediks step by step:
- Install an IP address scanner on your PC. We recommend using the Angry ip Scanner utility. This tool will allow you to find the IP addresses of a specific computer network.
- Next, you need to find an effective brute-utility. Most users use the DUBrut program when hacking. The program interface is intuitive, so even inexperienced users will not have problems using it.
- Select the dedicated server you plan to access.
After you have installed all the utilities necessary for hacking, you can start brute force:
- Launch the scanner and set up the selection criteria. Don't forget to specify the following value in the port section: 3389.
- After completing the scanning process, export the selected data to a separate file via File/Export File.
- Launch the brute-utility and fill in all the settings fields.After the brute process starts, you can go about your business, since selecting data from the Dedik will take a lot of time.
- When finished, open the file good.txt, where all the data from the brute will be stored.
Despite the fact thatany program for hacking the servercan be used, the basic steps for obtaining free Dedik will be largely similar to the instructions described.
Many users are interested in the question of hacking game servers, so the request «program for hacking minecraft servers» occurs quite often.
For example, on the pagehttp://minecraft-cube.ru/skachat-programmu-minecraft-hackthere are detailed instructions for using the program «Minecraft hack», which is often used by many players.
As a result, we note that hacking a dedicated server does not require much effort if you have detailed instructions and all the necessary programs at hand.
If you do not have enough experience to hack on your own, we recommendthat you familiarize yourself with the video manuals on the YouTube video hosting site.
In any case, ready-made Dedik can always be purchased on the main page of our store.
In general, purchasing aready-made server accountis much easier than debugging it yourself.
Service presentation - how to place an order!
Similar materials on this topic
With the development of the Internet, a huge number of new terms began to appear. If earlier the meaning of the words «browser», «proxy», «bot» were little known. Nowadays, Internet users constantly have to deal with these terms. Dedik is also a dedicated...
more details ⟶When promoting their product or online project, many use a dedicated server for these purposes. Account brute process, flooding, advertising mailings to user bases – all this significantly reduces the performance of a personal computer. In this case, it is logical to use «dedik&raq...
more details ⟶



















